Last Updated on January 20, 2019 by Admin
IT Essentials Final Exam Answers Form A v6.0 2018 2019 100%
Cisco ITE latest or IT Essentials v6.0 Final Exam Answers Form A PC hardware and software (ITE Version 6.00) collection year 2017, 2018 and 2019 Full 100%. IT Essentials has been know as ITE. The following are the questions exam answers. Guarantee Passed. ITE v6.0 Final exam answers Form A has some new update from the old version 5. You can review all Final Exam Answers Form A. You will get passed scored 100% with this version 6.0. Good Luck for ITE v6.0 Exam!
Learning with Cisco Netacad, there are many exams and lab activities to do. Some instructor require students to complete all Chapter exams, Pre-Test, Practices Final, Final Exam and Chapter Quiz. No mater what instructors want you to do, examict.com offers all exams and lab activities answers and solutions with clear explanation. Our Experts have verified all exam answers before we published to the website. We recommended you to chose any relevant chapter from the following:
-
Why do laptop computers use CPU throttling techniques?
- to enhance the performance of the CPU
- to reduce the heat that the CPU may generate
- to ensure the CPU is running at its peak speed
- to conserve the battery life by reducing the bus speed between the CPU and RAM
Explanation: CPU throttling is used to conserve power and increase battery life on portable devices. Throttling also produces less heat.
-
What is the purpose of RAID adapters?
- to allow older PCI technology expansion slots to be used
- to provide enhanced audio and graphic capabilities
- to connect multiple storage devices for redundancy or speed
- to connect peripheral devices to a PC to improve performance
Explanation: RAID 0 allows “striping” or writing data across two hard drives, but provides no redundancy. The other RAID versions provide redundancy.
-
Which type of interface should a customer choose if connecting a single cable from a Microsoft Windows computer to output both audio and video to a high definition television?
- DVI
- HDMI
- PS/2
- DB-15
Explanation: The high definition multimedia interface or HDMI connector is used for outputting both audio and video on a single cable. A PS/2 port connects a keyboard or a mouse to a computer. Digital visual interfaces and DB-15 connectors are only used for video output.
-
What tool is included in the Mac OS X for backing up disks to image files and recovering disk images?
- Disk Utility
- Deja Dup
- Disk Error-Checking
- System Restore
Explanation: The Mac Disk Utility allows an administrator to configure automatic disk backups. The Deja Dup tool is a tool built into the Linux OS for backing up data. Disk Error-Checking is a Windows tool for checking the integrity of files and folders. The System Restore tool is a Windows tool for allowing an administrator to roll back the operating system to a previous configuration.
-
A new technician has joined the IT team and is about to service a heavy printer. Which two precautions should be taken to avoid any injury when transporting the heavy printer to the service area? (Choose two.)
- Avoid lifting the equipment using the strength in your back.
- Lift the equipment using the strength in your legs and knees.
- Avoid bending your knees when lifting the printer.
- Bend your back to pick the printer up.
- Avoid lifting the printer close to your body.
Explanation: When lifting heavy objects, avoiding bending or using the strength of the back, keeping heavy weights close to the body when carrying them, and using the strength of the legs and knee to lift something, all contribute to avoid injury.
-
What type of device provides power to a computer and allows it to be safely shut down in the event of a power loss?
- surge suppressor
- uninterruptible power supply
- standby power supply
- power inverter
Explanation: An uninterruptible power supply or UPS contains a battery backup that provides consistent power through brownouts and blackouts until the battery power is emptied. Many UPS systems can safely shut down a computer prior to the loss of battery power.
-
Which measure can help control RFI effects on wireless networks?
- Ensure the humidity and temperature levels are set as low as possible.
- Ensure the number of wireless NICs exceeds the number of wireless phones.
- Ensure the wireless network is on a different frequency than the offending source.
- Ensure each wireless NIC is configured to operate at different frequencies from all other wireless NICs.
Explanation: A wireless network (IEEE 802.11) can be affected by radio frequency interference because it shares the same radio frequency range with other devices, such as cordless phones.
-
What can be tested with a digital multimeter?
- wireless signal strength and access point positioning
- basic functionality of computer ports
- copper cable location
- quality of electricity in computer components
Explanation: A digital multimeter can test the integrity of circuits and the quality of electricity in computer components.
-
When should a technician avoid wearing an antistatic wrist strap?
- when installing RAM
- when replacing a power supply unit
- when installing a hard drive
- when opening a computer case
Explanation: A power supply unit or CRT monitor are both able to retain large amounts of power after being turned off. These types of devices are too dangerous to connect an antistatic wrist strap to. Antistatic wrist straps are commonly worn when upgrading RAM or replacing a hard drive.
-
Refer to the exhibit. As part of the process of building a computer, what is the proper order of the first three steps in the installation of a power supply?
- Steps 1, 2, 4
- Steps 1, 3, 2
- Steps 1, 4, 3
- Steps 2, 3, 4
Explanation: The steps for installing a power supply are as follows:
- Insert the power supply into the case.
- Align the holes in the power supply with the holes in the case.
- Secure the power supply to the case with screws.
Power is not applied until all components have been installed.
-
Which two operations can help prevent a mobile device from being tracked without permission? (Choose two.)
- Turn off the GPS when not in use.
- Use a VPN connection whenever possible.
- Set the device to not store credentials.
- Set the device to connect only to known WiFi networks.
- Disable or remove apps that allow connections to the GPS.
Explanation: Device tracking relies on GPS function. Turning off the GPS when not in use and disabling or removing apps that use the GPS function may prevent a device from being tracked.
-
What is a characteristic of a computer power connector?
- A Molex power connector supplies power to a motherboard.
- A Molex connector and a SATA connector can be used on the same drive at the same time.
- A SATA power connector is used to connect to a hard disk drive or an optical drive.
- An ATX main power connector supplies power to a video adapter.
Explanation: Hard disk drives and optical drives that do not have SATA power sockets use a Molex power connector. A Molex connector and a SATA connector cannot be used on the same drive at the same time. An ATX main power connector provides the motherboard with power from the power supply.
-
Which expansion card can assist in troubleshooting a computer problem when no video is available?
- BIOS card
- advanced graphics card
- USB expansion card
- POST card
Explanation: A POST card can be installed into a PCI or PCIe slot on the motherboard. When the computer encounters errors on startup, an error code is displayed on the card. Graphics cards and USB expansion cards do not have this ability. BIOS is found on a chip on the motherboard.
-
Which two PC settings can be configured using the BIOS setup utility? (Choose two.)
- POST
- virtualization support
- allocation of memory to applications
- enabling device drivers
- boot sequence
Explanation: The computer boot sequence and support for virtualization can configured from within BIOS. The computer operating system typically allocates memory to applications and enables device drivers. POST is typically not configurable.
-
What factor should be taken into consideration more with laptops than with desktops?
- environmental control
- loose cables
- short circuits
- unseated adapter cards
Explanation: Laptops are designed to be mobile and will most likely be used in situations that lack both environmental control and air filtration. Desktop computers are designed to be permanent workstations and are more likely to be used in controlled environments.
-
What are three benefits of computer preventive maintenance? (Choose three.)
- elimination of the need for repairs
- improvement in data protection
- extension of the life of components
- reduction in the number of equipment failures
- time savings for technicians making repairs
- improvement in RAM access time
Explanation: Preventive maintenance can reduce the need for future repairs, but cannot eliminate them entirely. Preventive maintenance does not affect a technician making repairs. Preventive maintenance has no effect on RAM access time. The remaining options are all benefits of performing preventive maintenance.
-
Which step in the troubleshooting process is important to help avoid repeating repair processes that were performed previously?
- identification of the problem
- implementation of the solution
- documentation of the problem and its solution
- preparation of a plan of action
-
A computer user complains of a computer that freezes up after about five minutes of use. The technician checks the computer BIOS to see if there might be a configuration problem that is causing the computer to behave consistently in this manner. While the technician is reviewing the information, the computer once again freezes. What is the probable cause of the computer problem?
- The BIOS is corrupt.
- The hard drive is failing.
- The CPU fan is not functioning.
- The CMOS battery has failed.
Explanation: A problem with the CPU or overheating can cause the computer to freeze.
-
Why is a full format more beneficial than a quick format when preparing for a clean OS installation?
- A full format is the only method of installing Windows 8.1 on a PC that has an operating system currently installed.
- A full format will delete files from the disk while analyzing the disk drive for errors.
- A full format will delete every partition on the hard drive.
- A full format uses the faster FAT32 file system, whereas a quick format uses the slower NTFS file system.
Explanation: A full format removes files from a partition while scanning the disk for bad sectors. A quick format will remove files from a partition but does not scan a disk for bad sectors.
-
What is the default file system used during a fresh installation of Windows 7?
- NTFS
- HPFS
- FAT16
- FAT32
Explanation: While Windows XP can use either FAT or NTFS, Vista and Windows 7 can only be installed on an NTFS partition.
-
What is the first step an administrator should take when splitting a single partition into multiple partitions?
- Format the partition.
- Assign a drive letter to the partition.
- Extend the partition.
- Shrink the partition.
Explanation: The first step in the process of splitting a partition is to use the shrink volume feature of the Disk Manager utility. Afterwards, the new partition must be formatted and assigned a drive letter.
-
A user notices that some of the programs that are installed before upgrading Windows to a new version no longer function properly after the upgrade. What can the user do to fix this problem?
- Use the System Restore utility.
- Update the driver for the graphics card.
- Run the programs in Compatibility Mode.
- Use the recovery partition to reinstall Windows.
Explanation: Compatibility mode allows an application designed for an earlier version of Windows to operate in later versions. Right-click on the command that starts an application and select Properties to access compatibility mode.
-
A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Task Manager
- Add or Remove Programs
- Event Viewer
- System Restore
Explanation: Use the Task Manager Performance tab to see a visual representation of CPU and RAM utilization. This is helpful in determining if more memory is needed. Use the Applications tab to halt an application that is not responding.
-
A technician has installed a new sound card in a PC but it is not operating correctly. Where should the technician look to investigate driver problems?
- Computer Management
- Device Manager
- My Computer
- System Tools
Explanation: Device Manager can be used to view information about a particular piece of hardware, to view the driver version, to update the driver or roll it back, or to disable/enable a particular device.
-
After a Windows operating system has been installed, which program would a technician use to select the programs that will run at startup?
- Ntldr
- Regedit
- Msconfig
- Task Manager
Explanation: Msconfig is a system utility that can be used to performs diagnostic procedures on the Windows startup files.
-
Which type of network spans a single building or campus and provides services and applications to people within a common organizational structure?
- PAN
- WAN
- LAN
- MAN
Explanation: A LAN is smaller or more contained than a WAN, which can span several cities. A MAN is usually contained in one city. A PAN is a very small network of devices that are located in close proximity to one another, usually within range of a single person.
-
A network administrator has finished migrating from a peer-to-peer network to a new client-server network configuration. What are two advantages of the new configuration? (Choose two.)
- The total cost of the new solution is considerably lower.
- Data is more secure in the event of hardware failures.
- Individual users are in control of their own computers and network resources.
- Data resources and access are centrally controlled.
- Personnel costs are lower because a dedicated network administrator is no longer necessary.
Explanation: Centralization in a client-server network configuration provides better monitoring for security, as well as easier access to resources. The total cost may be higher because a network administrator is required, but reliability and scalability are enhanced.
-
What are the four layers in the TCP/IP reference model?
- application, presentation, internet, network access
- application, transport, network, data link
- application, transport, internet, network access
- application, presentation, session, transport
- physical, data link, network, transport
-
Several messages sent to the network administrator are reporting that access to a secure server using HTTPS is failing. After checking recent updates to the company firewall, the administrator learns that the firewall is blocking HTTPS. Which port should be opened to solve the problem?
- 22
- 53
- 80
- 143
- 443
-
A user wants to map a network drive on a PC that is named “WORK2” and runs Windows 7. The name of the shared resource the user wishes to map to is called “installs” and is located on a workstation called “WORK1”. What would be the correct path for mapping the network drive?
- \\ username\WORK2\\installs
- \\username\password/WORK1/installs
- // WORK2/installs
- \\work1\installs
- \\username\Work2\installs
- \WORK2|installs
Explanation: The correct path syntax for mapping a network drive on a PC is \\servername\sharename. Note that the path statement is not case sensitive. Please also note that back-slashes (“\”) are used in Windows path statements and that ‘servername’ is the name of the source or location of the resource.
-
A customer who travels frequently wants to know which technology is the most suitable for being connected to the corporate network at all times at low cost. Which network technology would a network administrator recommend?
- satellite
- ISDN
- cellular
- microwave
Explanation: A customer who travels frequently wants to know which technology is the most suitable for being connected to the corporate network at all times at low cost. Which network technology would a network administrator recommend?
-
What is the difference between cloud computing and a data center?
- A data center provides access to shared computing resources, wheras a cloud is a private on-premise facility that stores and processes local data.
- Cloud computing solutions are network resources and services provided to the clients through the use of services from data centers.
- The data center makes use of more devices to process data.
- Data centers require cloud computing but cloud computing does not require data centers.
Explanation: Cloud service providers use one or more data centers for services and resources such as data storage. A data center is a data storage facility located inside the company and maintained by the IT staff or leased from a co-location provider where the maintenance can be done by the provider or the corporate IT staff.
-
A user complains about being unable to connect to the wireless network. Which two actions should be part of troubleshooting the wireless connection? (Choose two.)
- Verify that the laptop is plugged into an electrical outlet.
- Reconfigure TCP/IP settings on the laptop.
- Reinsert the laptop battery.
- Try moving the laptop to different places to see if a signal can be detected.
- Verify in the laptop software whether any wireless networks are detected.
Explanation: Also check if the computer has a button that enables wireless connectivity.
-
A technician installed a network adapter in a computer and wants to test network connectivity. The ping command can only receive a response from local workstations. What could be causing the problem?
- The NIC driver is out of date.
- The operating system is not compatible with the remote sites.
- The TCP/IP protocol stack is not loaded.
- The default gateway is not set.
Explanation: In order to access remote networks, a host IP configuration must include the address of the device that will be used to access the Internet or other networks. Pings to remote networks will fail if the default gateway is incorrect. Because the user can access local hosts, there are no problems with the NIC or operating system.
-
An ISP help desk technician receives a call from a customer who reports that no one at their business can reach any websites or get their e-mail. After testing the communication line and finding everything fine, the technician instructs the customer to run nslookup from the command prompt. What does the technician suspect is causing the customer’s problem?
- improper IP address configuration on the host
- hardware failure of the ISR used to connect the customer to the ISP
- bad cables or connections at the customer site
- failure of DNS to resolve names to IP addresses
-
A technician is asked to configure the time that the system must be idle before the hard disk spins down on all the Windows-based laptops in the company. The technician configured the power options in Windows but it appears to have no effect. Where should the technician look to enable power management?
- Administrative Tools
- BIOS
- Command Prompt
- Safe mode
- System Registry
Explanation: Look for the ACPI power management configuration section in BIOS.
-
A technician needs to configure a Bluetooth headset for a laptop user. Which two steps should the technician take before installing the headset? (Choose two.)
- Remove the battery.
- Disconnect AC power.
- Enable Bluetooth in BIOS Setup.
- Ensure that the antistatic wrist strap is attached to a nonpainted portion of the laptop.
- Ensure that the laptop Bluetooth switch is enabled.
Explanation: When attaching any wireless device to a laptop, power does not have to be removed (either AC or the DC battery). Also, you do not have to worry about ESD when installing a wireless device.
-
What laptop component converts DC power to AC so that the display can illuminate?
- inverter
- backlight
- CCFL
- battery
- motherboard
Explanation: The backlight (using either CCFL or LED technology) illuminates the back of the display, but the inverter part is what does the conversion of DC to AC for that backlight.
-
Which closed-ended question would be appropriate for a technician to use to narrow down the possible problems on a laptop that will not power on?
- Can the laptop operate using the AC adapter?
- Have you changed your password recently?
- What software has been installed recently?
- What were you doing when the problem occurred?
Explanation: Open-ended questions help the technician to identify the issue by allowing the customer to elaborate on the issue.The answers of “What software has been installed recently?” and “What were you doing when the problem occurred?” are examples of open-ended questions. Closed-ended questions are used to narrow the focus of the problem. Closed-ended questions commonly have definite answers such as yes, no, a date, a time, or other specifics. Both questions of “Have you changed your password recently?” and “Can the laptop operate using the AC adapter? are closed-ended questions, but the one relevant to the computer not powering on is the one containing the inquiry about the AC adapter.
-
A technician is troubleshooting the appearance of flashing lines on a laptop screen. What are two possible causes of this distortion? (Choose two.)
- Power to the pixels has been removed.
- The display settings have been changed.
- The GPU is not cooling correctly.
- The LCD cutoff switch is damaged.
- The display is not correctly installed.
Explanation: When flashing lines are appearing on a laptop screen, the most common problems are an overheating GPU, faulty GPU, or a display that is not connected properly. When the power to the pixels has been cut off, pixels on the screen will appear dead. If the images on a laptop screen are distorted, a technician should verify that the display settings have not been modified.
-
A user downloads a widget onto his Android phone but is puzzled to see that when the widget is touched an app is launched. What is a possible cause?
- The user has downloaded a virus.
- The widget is corrupt.
- The security settings of the Android OS have been compromised.
- The widget is associated with the app and this is the normal behavior.
Explanation: Widgets are programs that when installed associate with the application they were built for. This will cause the application to launch when the widget icon is touched on the touchscreen of the Android device.
-
Which component uses the greatest amount of power on most mobile devices?
- LCD screen
- camera
- CPU
- media player
Explanation: The LCD screen consumes the most power on most mobile devices. The CPU, camera, and media player use power, but less extensively than the LCD screen does.
-
What is the purpose of using the MIME email protocol on mobile devices?
- to enable pictures and documents to be included in email messages
- to re-synchronize the email account with other devices
- to remotely lock the email account if the device is stolen
- to encrypt the email messages
Explanation: The MIME email protocol allows pictures and documents to be included in email messages.
-
What is an indication that the battery in a mobile device could become physically hazardous and should be immediately replaced?
- if the battery only supports the system for a reduced period of time
- if there are signs of swelling
- if the screen brightness begins to dim
- if the device feels warm to the touch
Explanation: Because a swelling battery is physically hazardous, it should immediately be replaced with a new one from the manufacturer.
-
A technician is explaining the differences between inkjet printers and laser printers to a customer. Which two comparisons should the technician make? (Choose two.)
- Inkjet printers are less expensive as an initial purchase than laser printers.
- A laser printer is significantly slower than an inkjet printer.
- Both laser and inkjet printers produce poor quality images.
- The laser printer output is dry after printing, but an inkjet printer may still have wet ink on the paper after printing.
- Inkjet printers use plain paper to make economical prints, but laser printers require more expensive thermal paper.
-
For cleaning a laser printer, what should be used to pick up excess particles of toner?
- a HEPA-capable vacuum
- a lint-free cloth
- isopropyl alcohol
- a damp cloth
Explanation: The toner used in a laser printer consists of microscopic particles. To effectively pick up these particles, it is recommended that a vacuum capable of High Efficiency Particulate Air (HEPA) filtration be used.
-
What characterizes a DDoS attack?
- Many hosts participate in a coordinated attack.
- Infected computers are called daemons.
- It is easy to identify the source of the attack.
- All hosts must be in the same geographic area.
-
Which two password control policies should an organization implement to ensure strong passwords? (Choose two.)
- Passwords should be set to expire every 60 days.
- Passwords should contain no more than eight characters.
- Passwords must contain encrypted characters.
- Passwords should contain letters and numbers.
- Passwords should contain only capital letters.
-
A computer technician has been asked to secure all Windows 7 computers by encrypting all the data on each computer. Which Windows feature should be used to provide this level of encryption?
- BitLocker
- EFS
- TPM
- Windows Update
Explanation: BitLocker is a Windows feature that can be used to encrypt the entire hard drive volume. Encrypting File System (EFS) is a Windows feature that can be used to encrypt files and folders linked to a specific user account. TPM is a specialized chip on the motherboard that stores information specific to the computer system such as encryption keys, digital certificates, and passwords. Windows Update is used to update the operating system, not to encrypt data.
-
The activity of a previously unknown program triggers an alert by Windows firewall. What three options will the user have for dealing with this event? (Choose three.)
- Keep blocking
- Unblock
- Ask me later
- Deny all
- Turn off
- Turn on
Explanation: If a program is blocked by Windows firewall, the user will be presented with three options for dealing with this event: Keep blocking, Unblock, or Ask me later.
-
A technician suspects that a security issue is causing problems with a computer. What two actions could be performed to test theories of probable cause when troubleshooting the PC? (Choose two.)
- Log in as a different user.
- Disconnect the computer from the network.
- Search helpdesk repair logs for more information.
- Discuss solutions with the customer.
- Ask the customer open-ended questions about the problem.
Explanation: Several actions can be taken by a technician when security issues are suspected as the possible cause of a problem with a computer. Logging in as a different user or disconnecting the PC from the network to isolate the cause of the problem are two possible actions.
-
A call center technician answers a call from a frequent customer who is known to be impatient and lacks experience with computers. The customer has an issue with an application that the call center supports. The customer informs the technician that the problem had been reported before but the original technician was rude, did not listen, and did not fix the problem. If the technician is confident that the problem can be resolved by increasing the amount of memory in the computer, what should the technician do?
- Tell the customer to install 2 GB of DDR3 PC3-10600 RAM.
- Explain that the original technician is no good and the supervisor will be told.
- Suggest that the customer purchase a new computer.
- Confirm the issues and give detailed instructions to solve the problem.
Explanation: When dealing with customers, a technician must show professionalism in all aspects. When explaining the solution to solve the problem, a technician should provide a simple step-by-step process of instructions. The technician should speak in plain terms and avoid the industry jargon.
-
What expectation is defined in the service level agreement between an organization and service vendor?
- guaranteed service response time
- maximum number of service calls per day
- chain of custody procedures
- communication etiquette rules
Explanation: The service level agreement, or SLA, is a legal agreement between an organization and a service vendor. The agreement is a binding contract that spells out service expectations of the service vendor. The SLA typically contains response time guarantees, part availability, and time of service availability.
-
In which circumstance should a level one technician initiate an escalated work order?
- when a customer appears to be very knowledgeable
- when a customer demands talking to a particular technician
- when a problem requires expertise from another technician
- when the technician cannot understand the problem as explained by the customer
Explanation: The primary responsibility of a level one technician is to gather information from the customer. The level one technician needs to accurately enter all the information into the work order. When the problems are very simple to resolve, a level one technician can take care of these without escalating the work order. However, when a problem requires the expertise of a level two technician, the level one technician initiates an escalated work order so that a level two technician will be involved to solve the problem.
-
An application appears frozen and is not responding to a mouse or the keyboard. What Windows OS tool can be used to stop the application?
- Event Viewer
- Task Manager
- Device Manager
- Disk Management
Explanation: In Task Manager, the application or process that is not responding can be identified and closed. Device Manager is used to manage devices and their drivers. Disk Management is used to manage the partition and file systems of storage devices. Event Viewer is used to review the alerts and notifications sent from the system.
-
Which two issues are likely to cause BSOD errors? (Choose two.)
- out-of-date browser
- RAM failing
- device driver errors
- lack of antivirus software
- power supply failure
Explanation: Device driver errors are the most likely cause of BSOD errors. Failing RAM can also create BSOD errors. Software issues such as browsers and antivirus do not produce BSOD errors. A power supply failure would prevent the machine from starting.
-
A user has installed a new FTP client on a computer, but is unsuccessful in connecting to an FTP server. Which two key pieces of information should the user ensure are configured correctly on the FTP client? (Choose two.)
- username
- password
- FTP client IP address
- FTP server IP address
- FTP client port number
- FTP server port number
Explanation: Without the correct connection information for the FTP server, file transfer services cannot occur.
-
A technician wants to allow users to backup and restore all the files on their computers, but does not want the users to be able to make changes to the system. How should the technician give users this functionality?
- Grant the users read permissions on all files.
- Give the users administrator rights on their computers.
- Make the users members of a group called Backup Operators.
- Check the Folder is Ready for Archiving box in the properties of each folder.
Explanation: It is better to grant permissions at group level than individual permissions. This way any member of a group would have the respective permissions to carry out the permitted tasks and allows for a tighter control of what the group members can do in a given environment. It also makes it easier to administer the environment.
-
A technician who is working on an employee’s laptop finds that a number of files that were encrypted on a network server drive are present on the laptop drive in unencrypted form. What could cause this problem?
- Encrypted files cannot be transferred across a network.
- The new computer doesn’t have an NTFS partition.
- The network proxy decrypted the data to scan it for malware.
- The sensitive data was transferred with the FTP protocol.
Explanation: When encrypted files are transferred to a new computer that is not using an NTFS formatted hard drive, the files will no longer be encrypted.
-
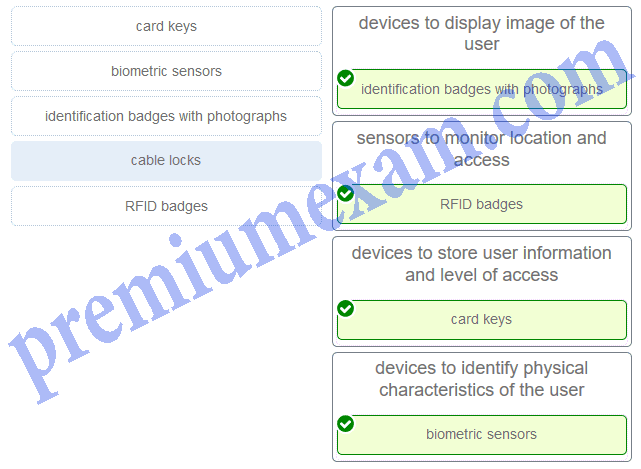
Match the facility access control devices to the correct descriptions. (Not all options are used.)
Learning with Cisco Netacad, there are many exams and lab activities to do. Some instructor require students to complete all Chapter exams, Pre-Test, Practices Final, Final Exam and Chapter Quiz. No mater what instructors want you to do, examict.com offers all exams and lab activities answers and solutions with clear explanation. Our Experts have verified all exam answers before we published to the website. We recommended you to chose any relevant chapter from the following: